

 |
||||||||||
|
How the Secure Socket Layer and certificates work
Certificates vouch for the authenticity of the site to confirm to a visitor that they are in the right place, and to protect data as it moves between the visitor and the site. Certificates are created with an encryption algorithm that uses a pair of keys, a public key and a private key. The public key may be given to anyone, the private key is held by the owner of the certificate. The key (no pun intended) to SSL is that Information encrypted with the private key may only be decrypted with the public key, and data encrypted with the public key may only be decrypted by the private key.
The verification of the certificate is a three part process. The certificate received from a Web site is doubly encrypted by the private key of the certificate authority and by the private key of the certificate owner.
-
If the public key of the authority, which is well known by all browsers, can be used to decrypt the certificate then it is a legitimate certificate vouched for by that authority. We also know at this point that the certificate, as encrypted by the authority, has not been tampered with.
-
The certificate itself contains the public key of the owner. If that public key properly decrypts the certificate then it must have been encrypted by private key which only the owner has. Now we know that the certificate originated from the owner, but how do we know the owner is sending it to us?
-
Finally, the browser encrypts a message (actually a third key which we will describe below) using the owner's public key and sends it back to the server. Only the legitimate owner has the correct private key to decrypt that message and act on it, so we must be talking to them!
The authentication of the certificate is visibly shown to the user by a padlock on the status bar of the Web browser. The detailed certificate information can usually be obtained by double-clicking on the padlock:
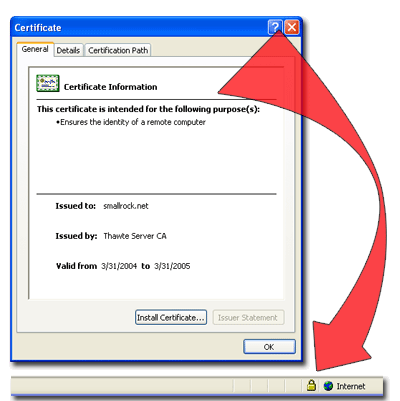
Any discrepancies in the certificate (cannot be decrypted, has an invalid key, is expired, or is coming from the wrong domain name) will cause the browser to complain about the certificate to the user. The user should be very suspicious of a web site providing a certificate that the browser has a problem with.
Once the browser is satisfied with the authenticity of the certificate and the source, the remainder of the data transmitted between the it and the site is protected using a randomly generated key known only to those two parties and another form of encryption, the Data Encryption Standard (DES). This encryption protects all data, including credit cards and other personal information. DES is used because it is more efficient than the public/private key encryption, but it has only one key that both sides need to have. DES could not be used without public/private key encryption to protect the randomly generated key as it is sent across the network.
Copyright © 2004 Smallrock Internet Services, Inc. All rights reserved.

